Table of Contents
When launching an ecommerce website, attracting the right customers is critical to its success. Many teams have goals and KPIs tied to lead generation and website engagement. The more high-quality traffic a website is able to attract, the more likely visitors are to turn into customers. However, recent studies have shown that 32% of direct and organic traffic to ecommerce sites comes from Invalid Traffic (IVT).
Invalid Traffic can be defined as any internet traffic that comes from bots, malicious human users, or suspicious human users.
This includes click farms, account hijackers, credit card fraudsters, shopper bots, and innocuous scrapers and crawlers. Regardless of the intent behind each threat type, all IVT is invalid and therefore cannot turn into real paying customers.
Since nearly a third of ecommerce traffic is made up of these bots and fake users, that can pose a variety of issues for retail marketers and go-to-market teams. Funnels become polluted with fake leads, bot traffic causes items to sell out in seconds before real customers have a chance to shop, and marketing analytics become skewed.
In this article, we will dive deeper into some of the most prevalent threats facing ecommerce marketers today and offer the right solutions to deal with these threats.
Table of Contents
6 Top Ecommerce Security Threats and Solutions
1. Click Hijacking
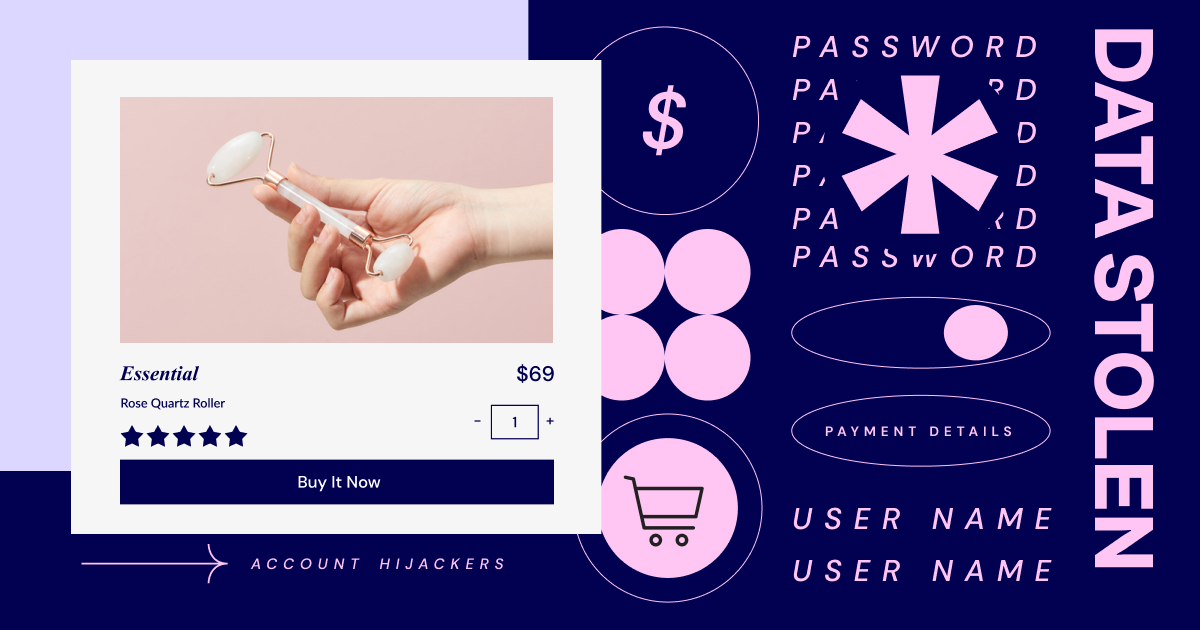
The threat: Malicious users can set up a call-to-action that appears legitimate when in fact, it’s a harmful link in disguise. When clicked on, the link causes that user to unintentionally download malware. This puts the user at risk of having their data stolen or their personal information exposed.
How this looks in ecommerce: Since fraudsters want users to click on their malicious links, they do their best to make them appear legitimate. Oftentimes, they will imitate a retail company and offer special discounts or other enticing offers. This can lead to customer trust and retention issues.
Furthermore, if a given ecommerce site has pop-ups or advertisements on its website from affiliates and partners, there is a chance some of those could be fraudulent links. In the example below, the links on the right-hand side go to affiliate websites, of which the original publisher may or may not know the legitimacy.
The solution: Retailers should ensure all advertisements and pop-ups on their sites are from legitimate businesses. If they are working with affiliates, they should be clear with those partners regarding the type of advertisers they will and will not allow.
Additionally, if a retail business notices other advertisers bidding against their company name and the links seem to go to questionable sources, those can be reported to the platform where you experienced this issue. For example, this could be Google Ads, LinkedIn Ads, Facebook Ads, or any other platform you are using.
2. Malicious Scrapers
The threat: Scrapers are robots that are designed to scan websites and collect data. Some are legitimate and are used for innocuous purposes, but others are designed and executed with harmful intent. When they scan a website for data and then use that data to disrupt business.
How this looks in ecommerce: Scrapers frequently arrive on ecommerce sites looking for specific pricing, product, and inventory information. If the bot is malicious, it can then duplicate product pages on another site; often listing the products at lower prices. So not only are these bots stealing customers from a legitimate site, they are often charging real customers for orders they have no intention of fulfilling.
The solution: Bots typically behave like bots, they move about a website in a way that does not appear human. They jump around quickly and haphazardly. If a business notices unusual activity on its website, it is wise to block that visitor from returning to prevent further fraudulent activity.

3. False Representation
The threat: This most often occurs when bots and malicious users try to modify their digital information in order to hide their identity. Bad actors do not want businesses to know their geolocation, their customer demographics, or anything else that might expose them to illegitimate behavior.
This is different from simply using a private browser or hiding behind a proxy; in these cases, information is specifically altered to make one user look like they have different characteristics than they do.
How this looks in ecommerce: When a bad bot or malicious user arrives on an ecommerce site, it can use false representation to make itself look like a legitimate customer. This makes them harder to detect as they move throughout a website, potentially committing fraudulent activity.
The solution: False representations can be difficult for the untrained eye to identify because of their very nature. Many times, cybersecurity or IT solutions need to be put in place to identify them in real-time. However, once fraudulent activity occurs from a particular user masking themselves with false representation, that user can be monitored or blocked from returning to the same page.
4. Account Takeovers
The threat: Account takeovers occur when a bot or malicious user hacks into a legitimate user’s account. This happens frequently on social media platforms, email providers, and even banking accounts.
How this looks in ecommerce: Many times, ecommerce sites allow returning customers to log into an account they’ve created in order to make shopping, shipping, and payment easier. However, if a malicious user hacks into that account, the results could be detrimental to both the business and the customer. Personal data often lives in these accounts and charges could quickly add up without the account owner knowing.
The solution: Accounts are less likely to be taken over by malicious users if there are protections in place. The use of CAPTCHA forms, security questions, and complex passwords can all make it slightly harder for malicious users to make it through to the other side.
5. Credit Card Fraud
The threat: Credit card fraud is committed by both bots and human users. It occurs when a fake card or stolen card is used to complete a purchase.
How this looks in ecommerce: If a malicious user steals a credit card and then makes a purchase on a given site, oftentimes the actual owner of that card will dispute the charge. This is a good thing for the real user, but bad for business. It causes inventory loss without compensation. Furthermore, if a bot uses a fake credit card and makes a massive amount of purchases on a site, not only does it cost the business revenue, but inventory is then depleted for real paying customers looking to buy.
The solution: First, make sure you are utilizing a protected Point-of-Sale system. Measures can also be put in place to ensure products are insured so that massive profits are not lost if fraud does occur. Malicious users can also be blocked from future purchases.

6. General Bot Traffic
The threat: In addition to the scrapers we previously mentioned, there are copious amounts of other bots across the internet. Some are purposely harmful, while others perform mundane tasks. However, since bots will never become human users, they should not be grouped in with regular customer traffic.
How this looks in ecommerce: Bots on ecommerce sites may scan for content or data, collect customer emails and then spam them with messages. They can also click on advertisements – either native to a site or on other platforms that drive traffic to the site – which drains budgets and optimizes campaigns toward illegitimate traffic.
The solution: Like malicious scrapers, general bot traffic can sometimes be identified by looking at user behavior on a website and noticing anomalies like sporadic clicking or unusual patterns of behavior moving from one page to another in a suspicious order. This can be seen in analytics platforms like Google Analytics and also through heatmap providers. Those users can then be blocked from returning additional times to a site.
Conclusion
IVT can take many forms on ecommerce sites, but education is the first step in protecting websites from fraudulent and malicious activity. Paying attention to user behavior, validating customer identities, and filtering out previously malicious users is a great place to start combating this issue.
However, keeping track of each individual visitor can be challenging, and sometimes impossible for enterprise businesses. If that is the case for your business, consider implementing go-to-market security for holistic protection.
Looking for fresh content?
By entering your email, you agree to receive Elementor emails, including marketing emails,
and agree to our Terms & Conditions and Privacy Policy.